Nethermind Interview (15-Minute Screen): What They Usually Test + How to Answer Clearly Without Sounding Rehearsed

The Nethermind “15-minute technical screen” looks small on a calendar. But it’s one of those rounds where good candidates still get rejected — not because they don’t know enough, but because their thinking doesn’t come out cleanly under time pressure.
In 15 minutes, the interviewer can’t validate “deep expertise” properly. What they can validate is whether you:
explain clearly (without hiding behind jargon),
draw decision boundaries (“when X vs when Y”), and
notice risk or assumptions naturally.
This isn’t an official Nethermind script — interview loops vary by team and role. But if you prepare using the structure below, you’ll usually avoid the most common failure pattern: rambling.
If you want the broader AOB interview map (so you don’t get lost), keep this hub open while you read:
https://artofblockchain.club/discussion/smart-contract-interview-prep-hub
TL;DR (read this twice)
The 15-minute screen is often a clarity + judgment test.
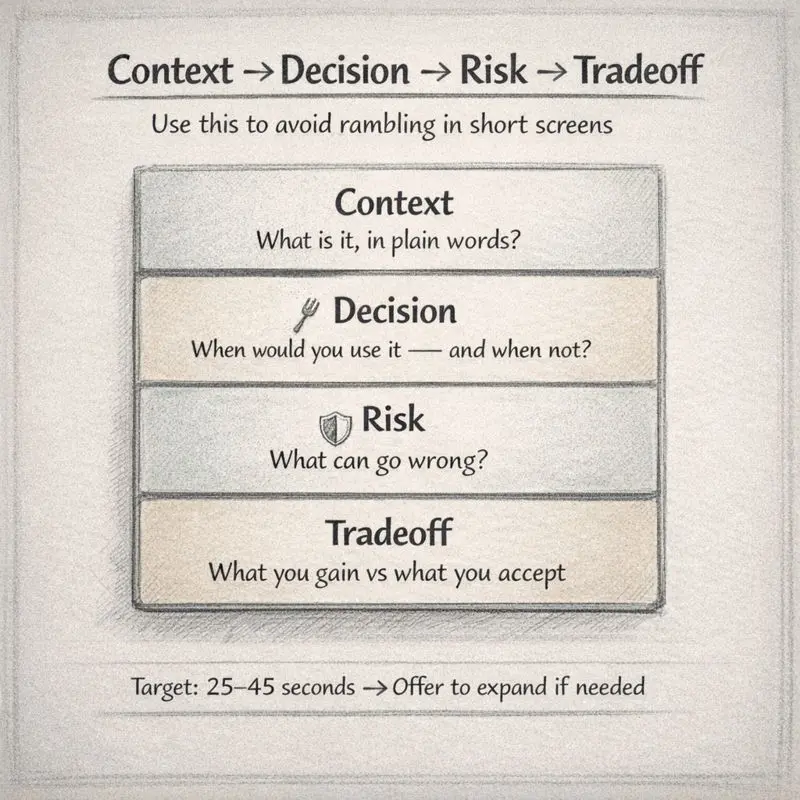
Your best weapon is a short answer structure:
Context → Decision → Risk → Tradeoff.
Prepare 5 “proof stories” from your work/projects, clean up fundamentals, and make your proof stack look like real thinking (not decoration).
If you want the “proof mindset” in one place:
https://artofblockchain.club/article/proof-based-hiring-in-web3-2025-how-founders-evaluate-github-tests-smart-contracts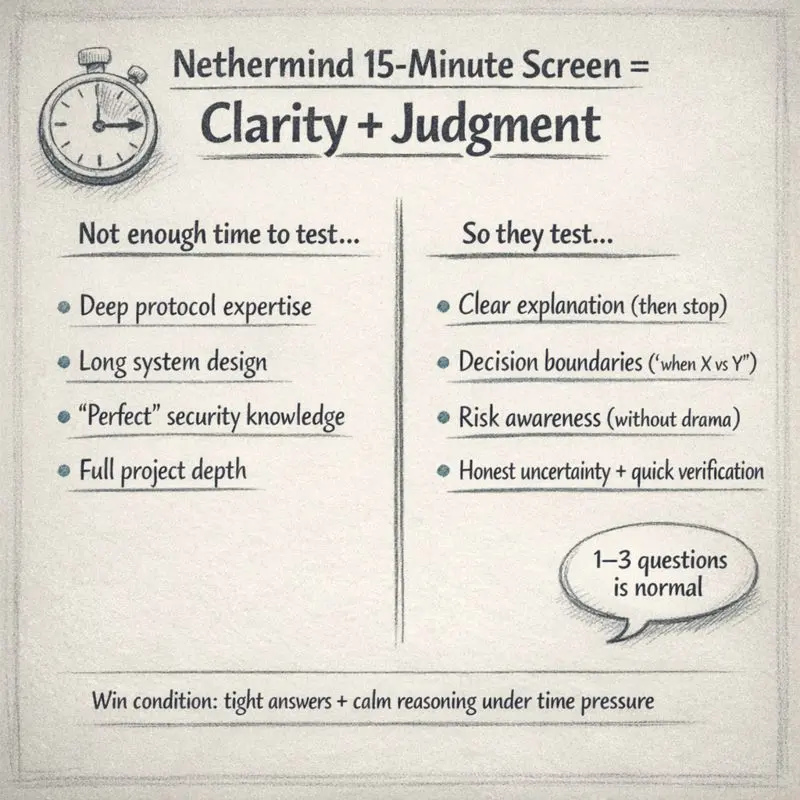
What interviewers are often testing in 15 minutes
1) Can you explain one idea simply and stop?
Many candidates keep talking because they’re trying to prove intelligence. In short screens, that usually backfires. A good answer feels complete even if it’s short.
2) Can you make decisions, not just describe tools?
“Foundry vs Hardhat” is not a useful answer unless you explain when you’d pick one and why. Senior candidates naturally say:
“It depends — here are the 2 factors that decide it.”
3) Do you notice risk without being dramatic?
You don’t need to act like an auditor. But Web3 teams care about security posture, so a candidate who naturally mentions risks (admin keys, upgrade mistakes, external calls) usually sounds more trustworthy.
If you need a structured refresher (without rabbit holes):
https://artofblockchain.club/discussion/smart-contract-security-audits-hub
4) Can you be honest without freezing?
A calm “I’m not sure, but here’s how I’d verify quickly” is usually a positive signal. Bluffing is a faster rejection.
The answer structure that keeps you from rambling
Use this for most short interview questions:
Context → Decision → Risk → Tradeoff
It forces your answer to stay tight and meaningful.
Context: what is it (1–2 lines)
Decision: when you’d use it (1–2 lines)
Risk: what can go wrong (1–2 lines)
Tradeoff: what you gain vs what you accept (1–2 lines)
This doesn’t make you sound “scripted.” It makes you sound organized.
Two model questions + short strong answers (use as practice)
*These are not “perfect answers.” They’re examples of tight answers that show judgment.*
Model Q1: “Explain upgradeability risk.”
Answer (30–40 seconds):
“Upgradeability lets you change logic while keeping the same contract address and state, usually via proxies. I’d use it when product iteration is needed, but only with clear governance and safeguards.
The main risks are storage layout mistakes, upgrade admin key abuse, and unexpected behavior changes after upgrades. The tradeoff is speed and maintainability versus operational and governance risk — so the upgrade process and monitoring matter as much as the code.”
Why this usually works: it names the concept, decision boundary, risks, and tradeoff without drowning in details.
If you want fundamentals that support answers like this:
https://artofblockchain.club/discussion/smart-contract-fundamentals-hub
Model Q2: “Explain reentrancy like you’re warning a teammate.”
Answer (25–35 seconds):
“Reentrancy happens when a contract sends value or makes an external call before it finishes updating its own state, and the external contract calls back into the original function while it’s in an unsafe intermediate state.
The risk is repeated withdrawals or state manipulation. Typical defenses are checks-effects-interactions, reentrancy guards, and careful external call placement. The tradeoff is sometimes design complexity or gas overhead, but it’s usually worth it for safety.”
Why this usually works: it explains the pattern, shows what can go wrong, and gives prevention options without sounding like a checklist.

A realistic 48-hour prep plan (no fantasy schedule)
If you’re close to the interview, don’t try to “learn everything.” You only need to do a few things well.
Step 1: Prepare 5 proof stories (your best leverage)
Write 5 short stories you can tell in 30–45 seconds each:
a bug you caught or prevented
a debugging incident
a design tradeoff you made
a security mistake you learned from
an optimization you shipped (performance/gas/latency)
These stories make you sound like someone who’s worked on real problems, even if you’re early in Web3.
Step 2: Cover the fundamentals that interviews often touch
Don’t over-study. Just make sure you’re safe on:
storage vs memory
access control patterns
msg.sender / tx.origin (why it matters)
external call patterns
upgradeability risks
Use this hub as a map:
https://artofblockchain.club/discussion/smart-contract-fundamentals-hub
Step 3: Clean up your proof stack (so you don’t look “course-only”)
A single strong repo + one writeup with reasoning often beats ten half-finished repos.
If you want how hiring teams read GitHub signals:
https://artofblockchain.club/article/how-recruiters-read-your-github-2025-building-proof-stacks-for-blockchain-trust
Common mistakes (and safer alternatives)
Mistake: “I know rollups / ZK / MEV” (no decision logic)
Safer: “I’ve used X; when choosing Y I consider these 2 factors…”Mistake: speaking for 90 seconds before answering
Safer: answer in 20 seconds, then offer to expandMistake: bluffing
Safer: “I’m not fully sure — here’s how I’d verify quickly”
If your goal is job search strategy beyond one interview:
https://artofblockchain.club/discussion/job-search-web3-career-navigation-hub

FAQs
Nethermind interview questions (15 minute screen)
They vary by team, but short screens often test clarity on fundamentals, risk thinking, and your ability to define tradeoffs quickly.
Nethermind 15 minute technical interview what to expect
Expect 1–3 questions maximum. The interviewer is often checking how you explain and how you reason, not running a deep technical drill.
How to prepare for Nethermind interview in 48 hours
Prepare proof stories, cover fundamentals, practice the Context→Decision→Risk→Tradeoff structure, and tighten your GitHub proof stack.
What does Nethermind test in the first technical round
Often: clarity, decision boundaries, basic smart contract/security reasoning, and honest communication under time pressure.
How to answer system design questions in a short interview
Answer with a boundary first: “It depends on X and Y.” Then give one tradeoff and one risk. Don’t try to teach a full lecture.
How to explain smart contract security clearly in interviews
Explain one failure mode in simple words, then state one mitigation and one tradeoff. Avoid listing 20 vulnerabilities like a memorized sheet.
What questions to ask at the end of Nethermind interview
Ask about first 30–60 day success definition, review culture, and how the team handles upgrades/incidents.
How to talk about GitHub in a short interview
Point to 1 repo and 1 writeup that shows your reasoning. Quantity doesn’t help if it looks shallow.
CTA
If you are struggling with your CV, connect with Artofblockchain.club
If you want to brush up your knowledge in fun way, our blockchain Quiz is the best place to hand out.
If you’re a hiring team and your JD attracts the wrong people, we JD Risk Score + rewrite, and feature your role in the hiring hub:
