Learn Zero-Knowledge Proofs (ZKPs) in 30 Days: A Beginner’s Roadmap

Learn Zero Knowledge Proofs in 30 days by following a structured roadmap: master cryptography, build ZK circuits, and apply zero knowledge to real blockchain projects. This guide breaks down the learning process into clear, actionable weekly steps for beginners and upskillers.
What Is Zero Knowledge?
Zero Knowledge Proofs (ZKPs) let you prove you know something without revealing the secret. This cryptographic method powers blockchain privacy, secure authentication, and scalable Layer 2 solutions like zk-Rollups.
Table of Contents
What Are Zero-Knowledge Proofs?
Why Learn Zero Knowledge?
30-Day Roadmap to Learn Zero Knowledge
Week 1: Core Concepts & Tools
Week 2: Protocol Implementation
Week 3: Hands-On ZKP Development
Week 4: Advanced Applications
Key Zero Knowledge Technologies
Frequently Asked Questions (FAQ)
Next Steps
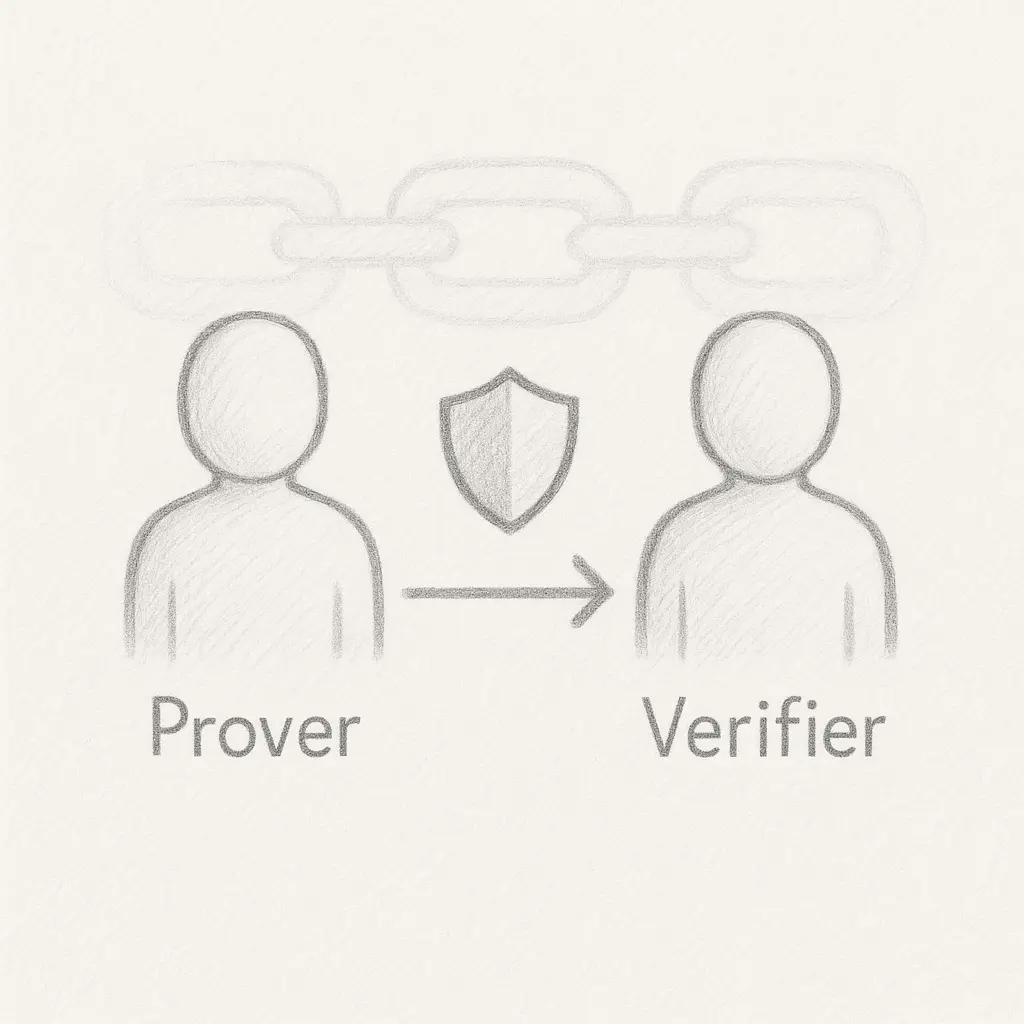
What is ZKP?
Zero-Knowledge Proofs are cryptographic protocols. They let a prover convince a verifier they know a value or secret, without revealing the value itself. This process ensures privacy and trust in digital transactions and blockchain systems.
Key Features:
Prove knowledge without exposing data
Enhance privacy and security
Enable trustless verification
Further Reading:
Why Learn Zero Knowledge in blockchain?
Learning Zero Knowledge Proofs unlocks advanced blockchain roles. You can design private transactions, build secure authentication, and contribute to next-gen scaling solutions. ZK skills are essential for blockchain developers, security engineers, and cryptography enthusiasts.
Benefits:
Build privacy-preserving apps
Work on Ethereum, Zcash, and Layer 2 platforms
Advance your blockchain career
Explore More:
Zero Knowledge Proof Explained: Privacy, zk-SNARKs, and Blockchain Applications
Week 1: Core Concepts & Tools
Days 1–3: Cryptography Fundamentals
Study hash functions (SHA-256, Keccak)
Learn symmetric (AES) and asymmetric (RSA, ECC) encryption
Understand digital signatures
Recommended Resources:
Days 4–7: ZKP Basics
Grasp interactive vs. non-interactive ZKPs
Use Ali Baba’s Cave analogy to visualize ZKPs
Explore real-world ZKP uses (privacy coins, authentication, zk-Rollups)
Start Here:
Week 2: Protocol Implementation
Days 8–11: zk-SNARKs
Learn how zk-SNARKs work (succinct, non-interactive proofs)
Understand trusted setup requirements
See zk-SNARKs in zk-Rollups for Ethereum scaling
Deep Dive:
Days 12–14: zk-STARKs
Study zk-STARKs (transparent, no trusted setup)
Learn about post-quantum security
Further Reading:
Week 3: Hands-On ZKP Development
Days 15–21: Circom and ZK Circuits
Get Started:
Week 4: Advanced Applications
Days 22–28: Real-World ZK Integration
Integrate ZKPs into smart contracts
Explore zk-Rollup solutions (zkSync, Polygon zkEVM)
Build private authentication systems
Further Exploration:
Key Zero Knowledge Technologies
Zk-SNARKs: Succinct, non-interactive proofs used for privacy and scaling in Ethereum and Zcash. Learn more at Consensys and ZKP Applications in Blockchain.
Zk-STARKs: Scalable, transparent, and post-quantum secure. Used in StarkNet and StarkWare. See AMINA Bank and ZKP Applications in Blockchain.
Circom: ZK circuit programming language for ZK app development. Get started with the Circom Tutorial for Beginners and Circom GitHub.
Zk-Rollups: Layer 2 scaling and batch transactions for Ethereum scalability. Learn more at zk-Rollups Explained and zkSync Docs.
Frequently Asked Questions (FAQ)
1. What is Zero Knowledge Proof (ZKP)?
A ZKP lets one party prove knowledge of a secret without revealing it, ensuring privacy and security in digital systems.
2. Does Bitcoin use ZKP?
Bitcoin does not use ZKPs by default, but some privacy-focused solutions experiment with them.
3. What are ZKP applications?
ZKPs power privacy coins, secure identity verification, confidential voting, and private smart contracts.
4.What are the steps in ZKP?
Setup: Establish proof parameters
Commitment: Prover sends proof
Verification: Verifier checks the proof without accessing the secret
Next Steps
Join ArtofBlockchain.club for more discussions, resources, and expert insights on blockchain careers.
Practice building ZK circuits and deploying ZK-powered apps.
Stay updated with the latest in zero knowledge and blockchain privacy.
