How to Crack Solidity Interviews in 2025: From Technical Prep to Career Growth

Solidity interviews in 2025 are a different challenge. Employers hiring for senior smart contract developer roles expect more than syntax knowledge. They want to see if you can design secure, gas-efficient, and production-ready contracts while understanding the bigger picture of Ethereum standards and DeFi systems.
For job seekers, this means interview prep can’t stop at memorizing code snippets. You need to connect technical answers with real-world scenarios, explain how you’d prepare a contract for an audit, and show awareness of the career landscape — from recruiter expectations to salary trends.
This guide brings it all together: the most common Solidity interview questions, strategies to answer them with confidence, and insights into what employers are looking for in Solidity developers in 2025.
📌 TL;DR
Security questions like re-entrancy, overflow/underflow, and delegatecall misuse remain core interview topics.
Gas optimization matters: explain trade-offs between storage vs memory, loops, and events.
Senior interviews test EVM awareness: low-level calls, opcodes, and sometimes inline assembly (Yul).
Companies expect knowledge of ecosystem standards like ERC-20/721/1155, plus DeFi design and audit readiness.
Solidity is a top-paying blockchain career — senior developers earn $120K–$200K+
with strong demand in DeFi, L2, and GameFi.
Recruiters look for a security-first mindset, testing frameworks, and audit culture as much as coding skill.
Best prep = mix of mock coding, open-source reviews, quizzes, and community discussions.
1. Security Questions in Solidity Interviews
When recruiters interview senior Solidity developers, the first area they test is almost always security. The reason is simple: one vulnerable smart contract can cost millions. Knowing the syntax of Solidity is not enough. Employers want to hear how you think about risk, design safe contracts, and prevent mistakes that still cause real-world hacks.
Re-entrancy Attacks
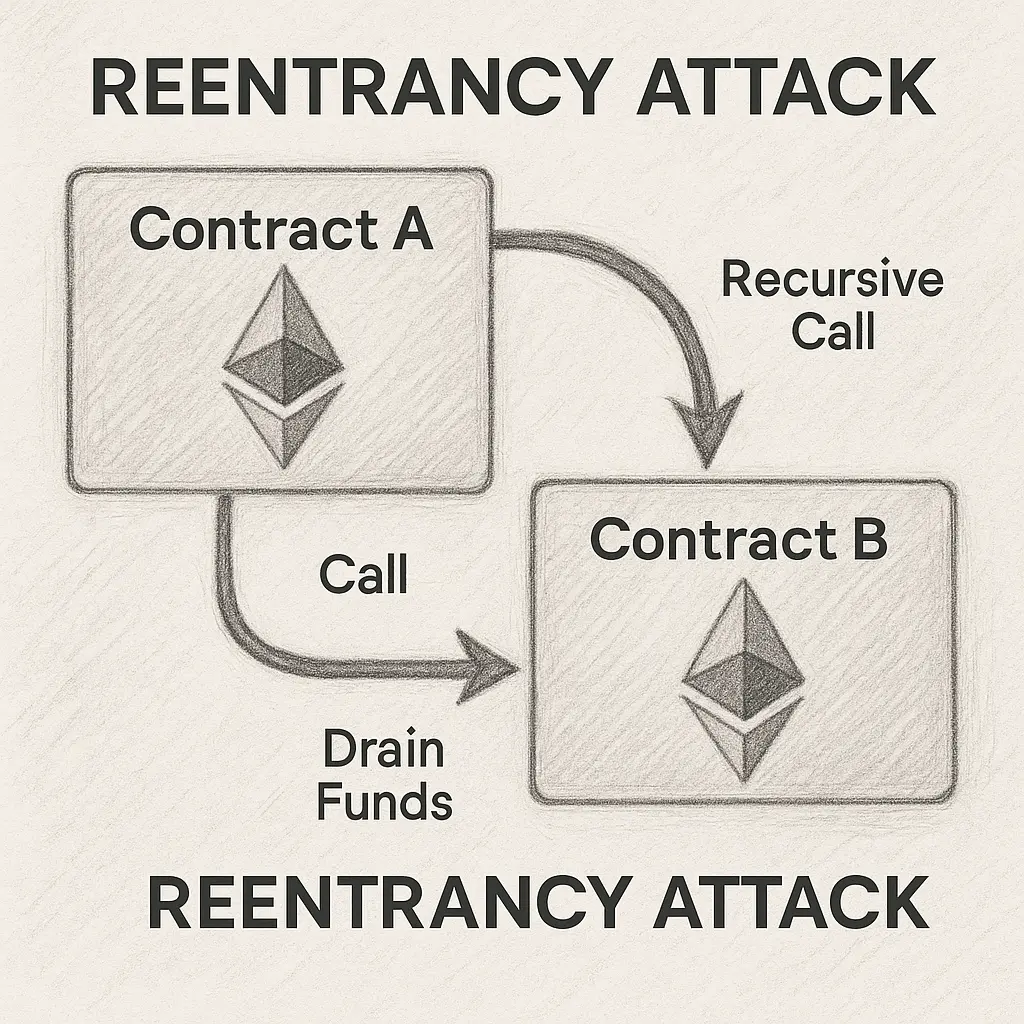 Re-entrancy attacks are one of the first things interviewers bring up in Solidity interviews. Instead of giving a textbook definition, explain the sequence: an attacker calls a vulnerable contract, that contract calls back into the attacker before updating its balance, and the process repeats until funds are drained.
Re-entrancy attacks are one of the first things interviewers bring up in Solidity interviews. Instead of giving a textbook definition, explain the sequence: an attacker calls a vulnerable contract, that contract calls back into the attacker before updating its balance, and the process repeats until funds are drained.
From there, walk through the defenses. Most developers highlight the checks-effects-interactions pattern, but strong candidates also mention the pull payment model and practical tools like OpenZeppelin’s ReentrancyGuard.
This isn’t just theory — The DAO hack in 2016 used exactly this vulnerability, and interviewers often expect you to connect your answer to that real case.
In our community thread on Solidity security expectations, developers share how interviewers often frame this question by referencing famous hacks such as The DAO exploit.
Integer Overflow & Underflow
Although Solidity ^0.8.x automatically checks for integer overflows, interviewers still ask about it. They want to see if you’re aware of legacy codebases and how SafeMath was once essential. Strong candidates explain:
how contracts compiled before ^0.8.x behave differently,
why auditors still test for these scenarios,
and how fuzzing tools in Foundry or Hardhat help catch arithmetic issues.
We’ve seen in practice that companies want to know if you’ll bring up both the old SafeMath approach and the new compiler checks, showing you can work with code from different eras. For a real-world discussion, check our community thread on overflow/underflow handling.
Delegatecall & Proxy Risks
Another favorite question is about delegatecall. Senior Solidity developers are expected to know not just what it does, but why it’s dangerous if used carelessly in proxy contracts. A typical interview scenario is: “What happens if a proxy contract using delegatecall is not properly initialized?” The correct answer highlights how uninitialized storage slots can be hijacked, leading to full control of the contract.
Mitigations include setting up initializer functions and using upgradeable libraries such as those from OpenZeppelin. For background, the Ethereum.org page on smart contract security explains why upgradeable contracts are especially sensitive to initialization flaws.
Role-Based Access Control
Most interviews also cover access control, since unauthorized function execution remains one of the most common causes of exploits. Candidates are usually asked how they’d design role management in a production system. It’s not enough to say “I’ll use onlyOwner.” Strong answers mention multi-signature governance, AccessControl modules, and the principle of least privilege.
Our discussion on version and dependency management also touches on this topic, because different Solidity versions influence which access control patterns are available and efficient.
2. Gas Optimization & Performance
If security is the first topic in Solidity interviews, gas optimization usually comes right after. Hiring managers know that poorly optimized contracts can make even a secure system unusable by driving up transaction costs. That’s why you’ll often face questions about how to write code that is not just correct, but also efficient.
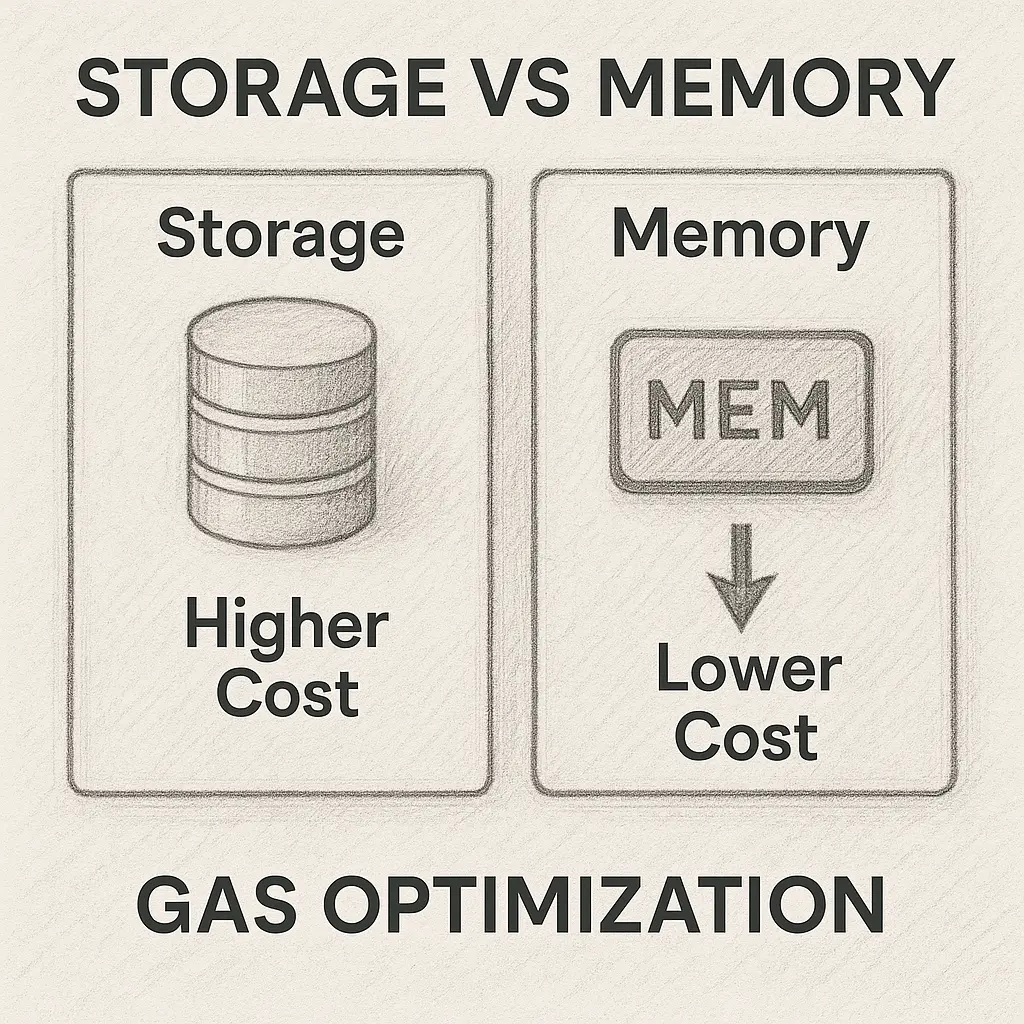
Storage vs Memory
A classic interview scenario is: “Why is using storage expensive compared to memory?” The answer lies in how Ethereum stores data. Reading and writing to storage means interacting with the blockchain’s permanent state, which costs far more gas than using temporary memory. Strong candidates explain how they move variables into memory when possible, while still being careful not to compromise functionality.
You can find more details in the Solidity docs on storage and memory. In our community discussions on Solidity version management, developers often highlight how compiler upgrades also influence gas rules for storage operations.
Looping & Computation Costs
Interviewers also like to ask: “What’s the gas impact of iterating over an array?” This tests if you understand that looping through large arrays on-chain is a design flaw. Senior developers are expected to suggest alternatives, like:
using mappings to enable O(1) lookups,
batching operations off-chain where possible,
or breaking processes into smaller transactions.
It’s not about memorizing costs but about showing you can redesign a contract to avoid scalability issues.
Events vs Storage Logging
Another subtle question is: “When do you store data on-chain versus just emitting an event?” Events are cheaper and widely used for transaction logs, but since they’re not directly accessible from other contracts, they’re not a replacement for all storage. Candidates who understand this trade-off — and can explain it clearly — stand out in interviews.
This kind of question separates junior coders from senior Solidity developers who think like system designers.
3. EVM & Advanced Design
Once you get past basic Solidity syntax and gas optimizations, many senior-level interviews dive deeper into the Ethereum Virtual Machine (EVM). Employers want to know if you understand how smart contracts actually run under the hood — because this is where subtle bugs, optimizations, and vulnerabilities are found.
Low-Level Calls
One question that comes up often is: “When would you use call, staticcall, or delegatecall instead of a normal function call?” Good candidates explain that these methods give flexibility in interacting with other contracts, but they also come with risks. For example, call returns a boolean success flag that must always be checked, and delegatecall executes in the caller’s context, which can expose storage slots if misused. Being able to explain both why you’d use them and how you’d secure them is a sign of senior-level understanding.
Opcode Awareness
Some interviews go further and test whether you know the gas cost of common opcodes. You don’t need to memorize all of them, but awareness of things like:
SLOAD (read from storage),
SSTORE (write to storage),
CALLDATA (reading transaction input)
…shows that you can design contracts with efficiency in mind. Employers want developers who think about costs before they ship production code.
Inline Assembly (Yul)
Another advanced topic is inline assembly, or Yul. Even if you rarely write Yul code in day-to-day work, interviewers sometimes ask: “When would you drop into assembly in Solidity?” The answer isn’t “because it looks cool.” It’s usually about gas-critical logic, handling cryptographic functions, or working around Solidity compiler limitations.
The Solidity docs on inline assembly give a good overview, but what impresses recruiters most is if you can connect Yul usage to practical scenarios. For example, developers in our community discussions on Solidity debugging often point out that dropping to Yul can make certain EVM error traces more understandable when debugging complex contracts.
👉 By this stage, the interview isn’t about “can you code in Solidity?” It’s about whether you understand the execution environment itself — the EVM. Candidates who can explain opcodes, low-level calls, and Yul in a way that connects to real-world development and audits usually leave a strong impression.
4. Ecosystem & Standards
By the time you’re at the senior interview stage, most companies expect you to understand Solidity in the context of the wider Ethereum ecosystem. It’s no longer enough to just explain contract syntax — you need to show how different standards and patterns connect to real-world use cases.
Consider the case of flash loan exploits on lending protocols in 2020. Interviewers may ask how you’d secure an oracle to prevent manipulation. A strong answer ties back to using Chainlink price feeds or implementing circuit breakers that pause the protocol under abnormal conditions.
Token Standards (ERC-20, ERC-721, ERC-1155)
A classic question is: “What’s the difference between ERC-20, ERC-721, and ERC-1155?” On the surface, it seems simple — fungible tokens, NFTs, and multi-token contracts. But interviewers want more than definitions. They want you to compare design trade-offs:
ERC-20 is lightweight but doesn’t support unique items.
ERC-721 is flexible for NFTs but expensive when minting in bulk.
ERC-1155 introduces efficiency for batch transfers, which makes it common in gaming and marketplaces.
Candidates who can also reference where they’ve seen these standards used in production — say, DeFi tokens, NFT collections, or GameFi platforms — leave a stronger impression.
📖 External ref: OpenZeppelin Token Standards
DeFi & Real-World Scenarios
In many interviews, you’ll be asked how you’d design something like a staking pool, lending protocol, or AMM. The goal isn’t to get you to code it on the spot but to see if you think about security-first design. Strong answers cover points like:
preventing flash loan exploits,
securing against oracle manipulation,
and designing contracts that can evolve as DeFi protocols grow.
This is where you can differentiate yourself from candidates who only studied syntax tutorials. Referencing real incidents such as lending protocol liquidations or AMM arbitrage exploits, shows you understand how Solidity connects to financial risk.
📌 Internal link: Overflow/underflow handling discussion — often flagged in audits of DeFi protocols.
Audit Readiness
Another sign of a senior developer is knowing how to prepare a project for an external audit. Recruiters may ask: “How do you get your contracts ready for auditors?” A strong answer mentions:
writing unit and fuzz tests,
documenting assumptions and threat models,
using standardized libraries like OpenZeppelin before reinventing the wheel.
Audit awareness matters because many companies hiring Solidity developers either run regular security reviews or work directly with external firms. Knowing what auditors look for tells an employer you’re used to professional development practices.
📖 External ref: Consensys Diligence – Smart Contract Auditing
👉 By the time an interviewer finishes these questions, they’ll know if you’re just a coder or if you’re a system-level thinker. Solidity careers in 2025 reward developers who can connect low-level contract design with ecosystem standards, DeFi use cases, and audit culture.
5. Career & Job Market Insights for Solidity Developers in 2025
Solidity developers remain some of the most in-demand professionals in Web3. But the job market in 2025 looks different from just a year or two ago. Companies hiring for smart contract developers now test more than coding — they want developers who can think like auditors, understand DeFi risks, and contribute to production-ready systems.
Career Ladder: From Junior to Senior
Recruiters often stress that senior Solidity roles are less about “can you code?” and more about “can you code securely and lead others?” In interviews, they look for signals like:
Have you worked with audit firms or reviewed real audit reports?
Can you explain trade-offs between frameworks like Hardhat and Foundry?
Do you understand how smart contracts interact with cross-chain bridges or Layer 2s?
For job seekers starting out, the path is usually:
Junior Solidity Developer: writing unit tests, basic ERC-20/721 implementations.
Mid-Level Developer: contributing to DeFi or NFT projects, debugging, gas optimizations.
Senior Developer: designing system architecture, reviewing security, mentoring juniors.
Specialist/Auditor: shifting into audit firms, protocol security, or smart contract architecture.
This ladder shows recruiters that you’re thinking about your career arc, not just passing one interview.
Skills Recruiters Value
Recruiters in 2025 look for more than syntax knowledge. The most common skills they highlight in job descriptions include:
Security-first mindset (handling re-entrancy, access control, overflow scenarios).
Gas optimization (efficient use of storage, loops, events). A common real-world example comes from NFT minting contracts in 2021–22, where poorly optimized loops caused users to pay hundreds of dollars in unnecessary gas fees. Companies still bring this up to test if you’d redesign arrays or use mappings instead of defending the inefficient approach.
Testing frameworks (Hardhat, Foundry, fuzz testing).
Cross-chain awareness (understanding how bridges, oracles, and L2 solutions interact with contracts).
Audit culture (writing clear tests and documentation).
In our community threads on Solidity interviews, job seekers often note that recruiters ask practical questions like: “How would you prepare a contract for an audit?” or “How do you handle version compatibility in Solidity?”
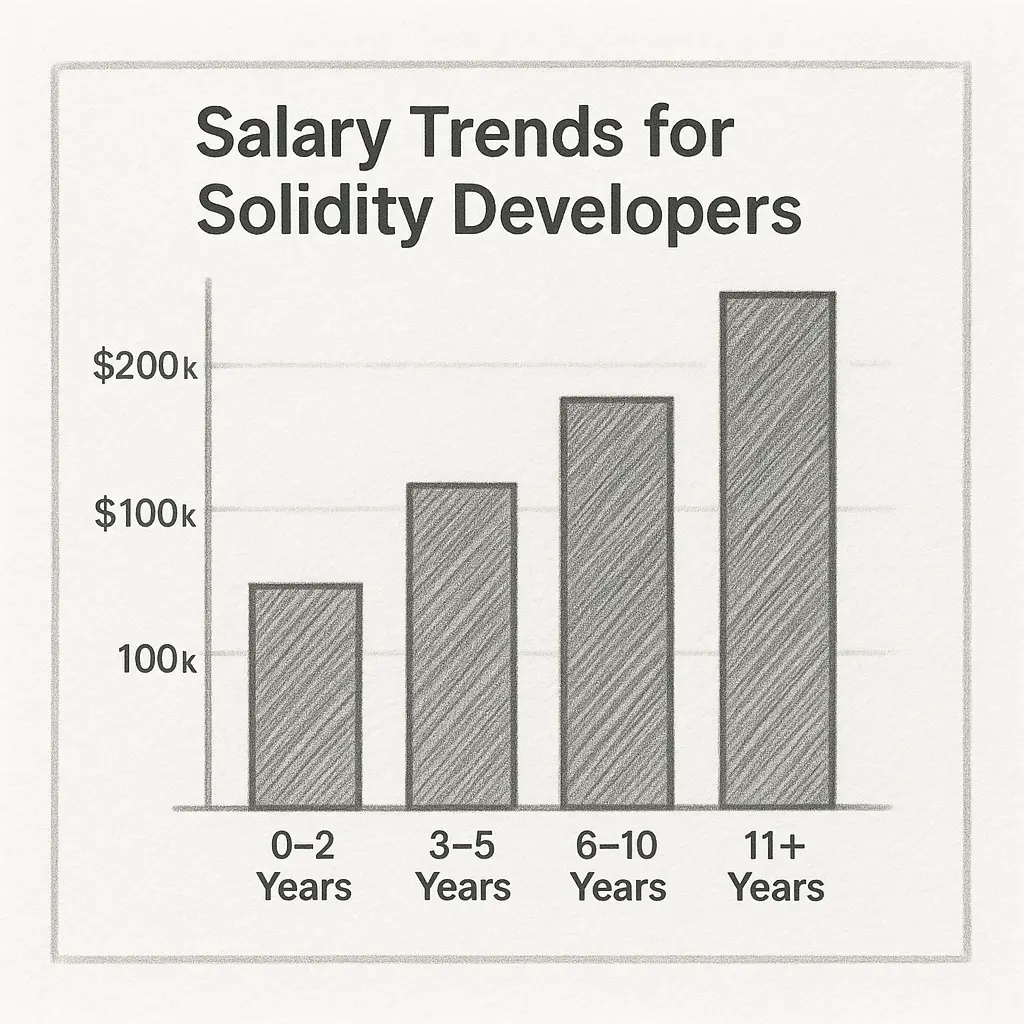
Salary Trends in 2025
As of June 2025, Web3.career and Glassdoor report that Solidity developers remain among the best-paid in Web3. Typical salaries are:
Junior Solidity Developers: $70K–$100K
Mid-Level Developers: $100K–$140K
Senior Solidity Developers: $140K–$200K+
Compensation is often higher in DeFi hotspots like the US, Singapore, and Dubai, especially where roles include token-based bonuses or equity. Remote roles remain strong, making this one of the most globally accessible tech careers.
📖 External references:
Demand Across Web3
The demand for Solidity talent has shifted towards DeFi protocols, Layer 2 ecosystems, and GameFi platforms. Remote roles continue to dominate, but companies are increasingly looking for developers who can also handle compliance, testing, and integrations with Web2 systems.
This makes Solidity one of the few blockchain careers that combines technical growth with long-term career stability.
6. Interview Preparation Strategies
Even if you know Solidity’s syntax and standards, the biggest challenge in interviews is showing your thought process under pressure. Recruiters want to see how you reason, not just whether you can write a contract that compiles.
One of the best ways to prepare is by practicing with mock questions in real tools like Hardhat and Foundry. For example, instead of just memorizing the definition of a re-entrancy attack, try writing a vulnerable contract, exploiting it locally, and then patching it. This kind of hands-on preparation gives you the confidence to explain solutions clearly in interviews.
Another smart approach is to study open-source contracts. Review how DeFi protocols or NFT marketplaces structure their code, look at their testing patterns, and note the security measures they use. Many candidates reference real audit reports or GitHub repos during interviews — which immediately shows they think like professionals, not students.
And of course, you don’t have to prepare alone. Our Solidity interview discussion threads are filled with experiences from developers who’ve been through the same questions you’re practicing now. Combine that with short, time-bound quizzes in the AOB Quiz Channel, and you’ll sharpen both your recall and your problem-solving speed.
📖 External ref: Hardhat Documentation
Conclusion
Preparing for a senior Solidity developer interview in 2025 is about much more than writing functions that compile. Employers test whether you can:
Anticipate security risks like re-entrancy and delegatecall misuse,
Design contracts with gas efficiency in mind,
Navigate the EVM and low-level details,
Understand ecosystem standards and DeFi patterns,
And present yourself as a developer who is ready for audits, real users, and production systems.
At the same time, Solidity is not just a technical career — it’s one of the most rewarding paths in blockchain jobs today. Salaries remain among the highest in Web3, and opportunities range from startups to DeFi giants to emerging Layer 2 projects. The best candidates combine technical depth with awareness of the career landscape.
👉 If you want to go beyond just reading guides, join the discussions onArtofBlockchain.club. Share your interview experiences, take daily quizzes, and keep an eye out for our upcoming blockchain job board, where we’ll connect job seekers with real opportunities across the Web3 space.
The best way to prepare for a Solidity career is not to study in isolation. It’s to learn, practice, and grow with the community.
📌 FAQs
Q1. What skills do I need to crack a senior Solidity interview in 2025?
You’ll need a strong grip on smart contract security (re-entrancy, access control, overflow handling), gas optimization, and knowledge of token standards like ERC-20, ERC-721, and ERC-1155. Employers also test your understanding of the EVM, testing frameworks like Hardhat/Foundry, and audit readiness.
Q2. Are Solidity developers still in demand in 2025?
Yes. Solidity remains one of the most in-demand blockchain skills, with demand coming from DeFi protocols, L2 solutions, and NFT/GameFi platforms. Many companies now look for developers who combine technical skill with security-first thinking.
Q3. How much do Solidity developers earn in 2025?
Senior Solidity developers typically earn $120K–$200K+ annually, depending on experience, geography, and token/equity-based compensation. Remote roles remain common, making it a global career option.
Q4. What’s the best way to prepare for Solidity interviews?
The best approach is hands-on: write contracts, exploit vulnerabilities in test environments, and patch them. Study open-source projects, read audit reports, and join communities like ArtofBlockchain.club where real candidates share interview experiences. Short quizzes also help sharpen recall under time pressure.
Q5. Is Solidity a good long-term career choice?
Yes. While other blockchain languages like Rust are growing, Solidity remains the backbone of Ethereum, DeFi, and most Layer 2 ecosystems. It’s a career path that combines strong salaries, global demand, and long-term relevance.
